Enterprise Recon Cloud 2.12.1
How To Setup Access Control List
We recommend using inbound rules to limit the ports allowed
to access the ER Cloud Master
Server. Refer to the Add Required Inbound Rules to the Security Group
section.
Access Control Lists allows you to limit access to ER Cloud from specific IP addresses.
Configure two access control lists:
- Web Console Access Control List: Limits Web Console access to computers that fall into a given range of IP addresses.
- Agent Access Control List: Limits Node Agents access to the Master Server if the Node Agent's IP address falls within a given range.
For example, allowing connections from IP address range 10.0.2.0/24 will allow traffic from IP address 10.0.2.0 – 10.0.2.255.
Configure the Access Control List
We recommend using inbound rules to limit the ports allowed
to access the ER Cloud Master
Server. Refer to the Add Required Inbound Rules to the Security Group section.
- Log in to the ER Cloud Web Console.
- In the Settings > Security > Access Control List page, go to the access control list you want to restrict.
- In the access control list that you want to change, enter the range of IP addresses and click +Add. A list of the IP address range you added is displayed under its respective access control list. For more information, refer to Access Control List Resolution Order below.
- For each IP address range added, you can
- Change the rule’s Access state from "Allow" to "Deny" and vice-versa.
- Remove specific rules.
- Clear All to remove all rules for that access control list.
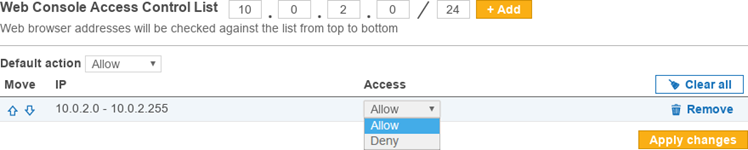
- To save changes to the rules, click Apply changes.
Access Control List Resolution Order
The range of IP address entered displays under its respective access control list section.
IP address ranges defined in these lists are resolved from top to bottom. If an IP address falls under two defined rules, the top-most rule takes precedence.
For example, the following rules:
1) 10.0.2.56 => Deny
2) 10.0.2.0 – 10.0.2.128 => Allow
3) 10.0.2.0 – 10.0.2.255 => Deny
resolve as:
10.0.2.56 => Deny
10.0.2.0 – 10.0.2.55 => Allow
10.0.2.57 – 10.0.2.128 => Allow
10.0.2.129 – 10.0.2.255 => Deny