Enterprise Recon Cloud 2.13.0
How To Install SSL Certificate
This section covers the following topics:
Overview
Your browser warns that the Web Console "uses an invalid security certificate". This is referring to the self-signed SSL certificate that the Master Server automatically generates upon deployment.
To prevent your browser from displaying the security certificate warning when connecting to the web console, you must add the certificate to the list of trusted Certificate Authorities.
To do this, you can either:
- Use Signed SSL Certificate, or
- Add the self-signed SSL certificate (that the Master Server automatically generates) to your computer’s list of Trusted Root Certificates (refer to Use Self-Signed SSL Certificates).
Use Signed SSL Certificate
To use a signed SSL certificate, you must:
- Assign a hostname to the Master Server. Refer to Assign Hostname to the Master Server IP Address.
- Obtain a new SSL certificate signed by a trusted Certificate Authority. Refer to Obtain Signed SSL Certificate.
- Add the certificate to trusted CAs and install the certificate. Refer to Add Signed Certificate to Trusted CA.
Assign Hostname to the Master Server IP Address
You must assign a host name in your domain to the ER Cloud Master Server IP address.
To do this, create a DNS A record for the ER Cloud Master Server in a domain that you own. If you don’t own a domain, you would need to purchase one from a public DNS hosting of your choice.
Depending on your public DNS hosting, you will usually need to enter the following information:
| Field | Description |
|---|---|
| IP address | Enter the PublicIP key value of your Master Server instance. Refer to the View the ER Cloud Instance section. |
| Host name | Enter the assigned host name for the A record (e.g. ercloud). |
| Domain | Enter the domain that you own (e.g. mycompany.com). |
Your ER Cloud PublicIP: 1.2.3.4
Hostname: ercloud
Domain: mycompany.com
The ER Cloud URL is ercloud.mycompany.com. You will use this URL to access the ER Cloud web console after you install the signed SSL certificate.
Obtain Signed SSL Certificate
Obtain a new SSL certificate signed by a trusted CA (certificate authority) by generating and submitting a Certificate Signing Request (CSR). This CSR is sent to the CA; the CA uses the details included in the CSR to generate the SSL certificate for the Master Server.
To obtain a signed certificate, perform the following steps:
-
On the Master Server console, generate a CSR:
# SSH to the EC2 instance ssh -i <path-to-the-sshkey.pem-file> ec2-user@<IP address or public DNS name>
# Copy the private key (sshkey.pem) file from the Master Server docker cp er2-master-server:/var/lib/er2/volume/sslkey.pem /home/ec2-user/sslkey.pem
# Generate the CSR openssl req -new -key sslkey.pem -out er2-master.csropenssl asks for the following information:
Prompt Answer Country Name (2 letter code) [AU]: Your country's two-letter country code (ISO 3166-1 alpha-2). State or Province Name (full name) [Some-State]: State or province name. Locality Name (e.g., city) []: City name or name of region. Organization Name (e.g., company) [Internet Widgits Pty Ltd]: Name of organization. Organizational Unit Name (e.g., section) []: Name of organizational department. Common Name (e.g. server FQDN or YOUR name) []: Must be the fully qualified domain name of the Master Server.
Make sure that the Common Name is the URL with which you access the Web Console. The Common Name depends on the URL you entered in your browser to access the Web Console (e.g. ercloud.mycompany.com). Refer to Assign Hostname to the Master Server IP Address above.Email Address []: Email address of contact person. Please enter the following 'extra' attributes to be sent with your certificate request - A challenge password []: Leave empty; do not enter any values. An optional company name []: Leave empty; do not enter any values. You must adequately answer the questions posed by each prompt (unless otherwise specified). The CA uses this information to generate the SSL certificate.The openssl command generates a CSR file, er2-master.csr.
-
Display and validate the contents of the CSR file.
openssl req -in er2-master.csr -text -noout -
Remove the private key (sslkey.pem) file.
rm -f /home/ec2-user/sslkey.pem -
Move the CSR file out of the Master Server (refer to Use SCP to Move the CSR File for general guidance) and submit the CSR file to your CA.
Use SCP to Move the CSR File
To move the CSR file out of the Master Server and submit it to a CA, use the SCP protocol.
On Windows
Use a Windows SCP client such as WinSCP to connect to the Master Server via the SCP protocol.
- Start WinSCP.
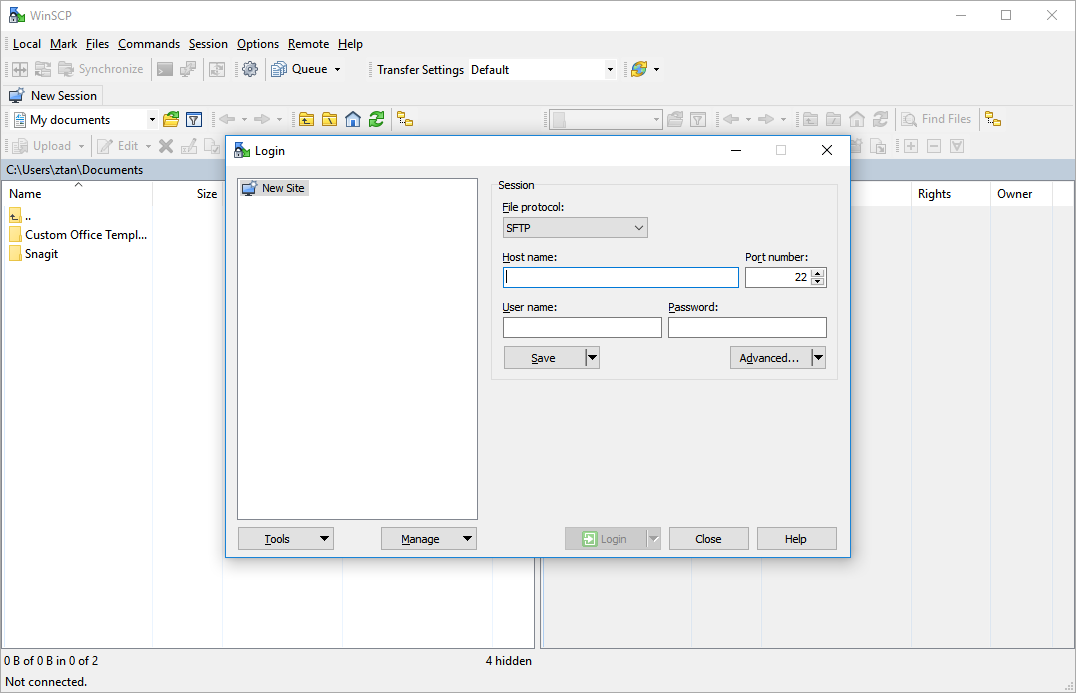
-
In the Login dialog box, enter the following:
Field Value File protocol Select SCP. Host name Enter the IP address or public DNS name of the ER Cloud EC2 instance. Port number Default value is 22. User name Enter ec2-user. Password Leave blank. - Click the Advanced… button.
- Under SSH section, click Authentication.
-
In the Authentication parameters section, click the … button and select the sshkey.pem file
The sshkey.pem file is the PEM file saved during deployment. Refer to the View the ER Cloud Instance section. - Click Save.
- Click Login to connect to the Master Server.
Once connected, locate the CSR file on the Master Server and copy it to your Windows host. Submit the CSR file to your CA.
On Linux
On the Linux host that you want to copy the CSR file to, open the terminal and run:
scp -i <path-to-the-sshkey.pem-file> ec2-user@<IP address or public DNS name>:/var/lib/er2/volume/er2-master.csr ./
This securely copies the CSR file (er2-master.csr) to your current directory. Once the file has been copied, submit the CSR file to your CA.
Add Signed Certificate to Trusted CA
The SSL certificate received from the CA must be added to the list of trusted CAs on the Master Server host. Once you have added the SSL certificate to the list of trusted CAs on the Master Server, you can install the new SSL certificate.
To do this, perform the following steps:
- Copy the SSL certificate received from the CA, usually a .cer or .crt file (e.g. ca.cert), to the Master Server (refer to Use SCP to Move the CSR File for general guidance).
-
SSH to the EC2 instance.
ssh -i <path-to-the-sshkey.pem-file> ec2-user@<IP address or public DNS name> -
Convert the SSL certificate (e.g. ca.cer) to .pem format.
# Syntax: openssl x509 -in <input-certificate-file> -outform PEM -out <output-pem-file> openssl x509 -in ca.cer -outform PEM -out sslcert.pemEnsure that the output file name of the SSL certificate is "sslcert.pem". -
(Optional) Display and validate the contents of the sslcert.pem file.
openssl x509 -in /var/lib/er2/volume/sslcert.pem -text -noout -
Copy the sslcert.pem file to the /etc/pki/ca-trust/source/anchors/ directory.
docker cp -a /home/ec2-user/sslcert.pem er2-master-server:/etc/pki/ca-trust/source/anchors/sslcert.pem -
Update the local trust store on the Master Server.
docker exec -u 0 er2-master-server update-ca-trust -
Install the new SSL certificate.
Instructions for installing the SSL certificate vary. Please check your CA’s official documentation for the installation procedure.# Set the correct permissions chmod 600 sslcert.pem
# Copy the sslcert.pem file to the er2-master-server:/var/lib/er2/volume directory docker cp -a /home/ec2-user/sslcert.pem er2-master-server:/var/lib/er2/volume/sslcert.pem
# Remove certificate rm -f /home/ec2-user/sslcert.pem -
Restart the Master Server.
/home/ec2-user/er-cloud.sh restart_master_server
After installing the signed SSL certificate, access the Master Server web console using the ER Cloud URL (e.g. ercloud.mycompany.com) without getting a security certificate warning.
Use Self-Signed SSL Certificates
The Master Server can act as its own CA and issue self-signed SSL certificates upon deployment. If you are using a self-signed certificate, you must add the certificate to the list of trusted Certificate Authorities (CA) to prevent your browser from displaying the security certificate warning.
To do this, you must:
- Extract the certificate. Refer to Extract Self-Signed Certificate from the Master Server.
- Add the self-signed SSL certificate to your computer’s list of Trusted Root Certificates. Refer to Add Self-Signed Certificates to Trusted CA.
Extract Self-Signed Certificate from the Master Server
To extract the auto-generated self-signed certificate from the Master Server, perform the following steps:
-
Copy the sslcert.pem file from the Master Server.
# SSH to the EC2 instance ssh -i <path-to-the-sshkey.pem-file> ec2-user@<IP address or public DNS name>
# Copy the sslcert.pem file from the Docker container docker cp -a er2-master-server:/var/lib/er2/volume/sslcert.pem /home/ec2-user/sslcert.pem -
Copy the sslcert.pem file to the Windows machine where you will access the ER Cloud web console.
Add Self-Signed Certificates to Trusted CA
After extracting the self-signed certificate from the Master Server, perform the following steps on the Windows machine where you will access the ER Cloud web console:
- On your keyboard, press and hold the Windows logo key + R.
- Enter certmgr.msc.
- Click OK. The certmgr console opens.
- On the right panel, right-click Trusted Root Certification Authorities.
- Select All Tasks > Import. The Certificate Import Wizard opens.
- Click Next.
-
Click Browse and navigate to the location where you copied the sslcert.pem file.
If you can’t find the file, ensure all file types in the folder are displayed by selecting All Files (*.*) from the dropdown list of file types next to the File Name field. - Click Next.
- Select the Place all certificates in the following store radio button then click Browse.
- Select Trusted Root Certification Authorities then click Next.
- Click Finish.
- Refresh the web console.
After adding the self-signed SSL certificate to the list of trusted CA, access the Master Server web console using the PublicDNS URL (of the ER Cloud instance) without getting the security certificate warning.