Enterprise Recon Cloud 2.13.0
How To Scan Network Storage Locations
This section covers the following topics:
- Overview
- Licensing
- Scan Windows Share
- Scan Azure File Share (SMB)
- Scan Unix File Share (NFS)
- Scan Using Remote Access via SSH
- Scan Hadoop Clusters
Overview
ER Cloud supports the following network storage locations:
- Windows Share
- Unix File Share (NFS)
- Remote Access via SSH
- Hadoop Clusters
For a more detailed explanation on network storage scans, refer to the Scanning - How Network Storage Scan Works section.
Licensing
For Sitewide Licenses, all scanned network storage Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, network storage Targets require Server & DB Licenses or Client Licenses, and consume data from the Server & DB License or Client License data allowance limit, depending on the Target operating system.
See Target Licenses for more information.
Scan Windows Share
Requirements
To scan a Windows share Target:
- Use a Windows Proxy Agent.
- Ensure that the Target is accessible from the Proxy Agent host.
-
The Target credential set must have the minimum required permissions to access the Target locations to be scanned.
Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
Add Windows Share Target
- From the New Scan page, add Targets. Refer to the Add Targets section.
- In the Select Target Type window, enter the host name of the Windows
share server in the Enter New Target Hostname field.
For example, if your Windows share path is \\remote-share-server-name\remote-share-name, enter the Target Hostname as remote-share-server-name:
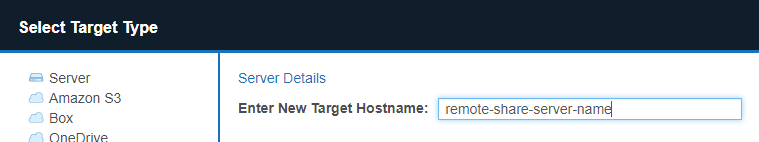
- Click Test. If ER Cloud can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, click on Network Storage.
- Under Network Storage Location Type, select Windows Share.
-
Fill in the following fields:
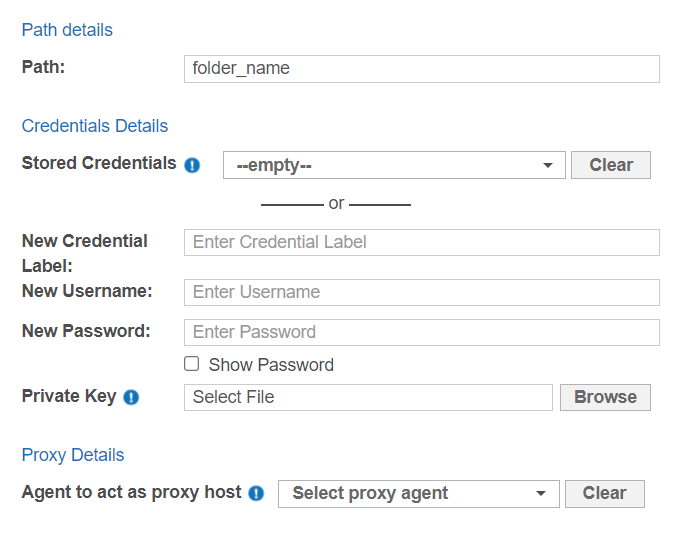
Field Description Path Enter the path of the folder to scan.
For example: <folder_name>Credential Label Enter a descriptive label for the credential set. Username Enter your user name.
For more information, refer to the Windows Target Credentials section below.Password Enter your password, or passphrase for the private key. (Optional) Private Key Upload the file containing the private key.
Only required for Target hosts that use a public key-based authentication method.
For more information, refer to the Set Up SSH Public Key Authentication section.Agent to act as proxy host Select a Windows Proxy Agent that matches the Target operating system (32-bit or 64-bit). - Click Test, and then + Add Customized to finish adding the Target location.
If the same location is recognized and scanned by ER Cloud separately as a different location and/or as a different protocol, ER Cloud will count the licensed data usage separately for each individual location.
To prevent redundant scanning and increased counting of licensed data usage, ensure that:
- the same location is not selected for scanning using both Local Storage and Network Storage protocols,
- both the shared folder and its subfolder are not selected for scanning if the subfolder is also shared separately,
- multiple shared folders (all pointing to the same physical location) are not included in the scan, and
- administrative shares are accounted for during location selection for the scan.
For more information and detailed scenarios, see Mitigate Increased Counting of Licensed Data Usage in ER2.
Windows Target Credentials
For scanning of Windows Share Targets using a Windows proxy agent, use the appropriate user name format when setting up the target Windows hosts credentials:
| Username | Description |
|---|---|
| <domain\username> | Windows target host resides in the same Active Directory domain as the Windows proxy agent. |
| <target_hostname\username> | Windows target host does not reside in the same Active Directory domain as the Windows proxy agent. |
Remediate Windows Share Targets
When remediating match locations on Windows Share Targets using the "Quarantine" option, you can specify a secure location on the Windows Share Target or Windows Proxy Agent host.
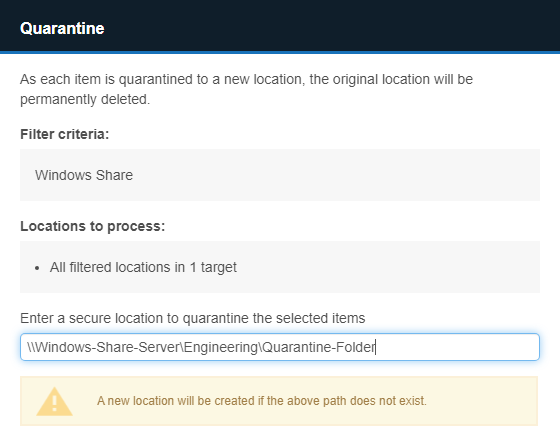
Use the following syntax in the "Enter a secure location to quarantine the selected items" field to specify the absolute path to a secure quarantine location on the:
-
Windows Share Target
# Syntax: \\<remote-share-server-name>\<remote-share-name>\<quarantine-folder> \\Windows-Share-Server\Engineering\Quarantine-Folder -
Windows Proxy Agent host
# Syntax: <quarantine-folder-on-proxy-agent-host> C:\Quarantine-Folder
Refer to the Perform Remedial Actions section.
Scan Azure File Share (SMB)
Azure file shares are scanned as a Windows share Target. Only SMB Azure file share is supported in ER Cloud.
Requirements
- Use a Windows Proxy Agent.
- Ensure that the Target is accessible from the Proxy Agent host.
-
The Target credential set must have the minimum required permissions to access the Target locations to be scanned.
Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
Get Azure File Share Credentials
- Log in to your Azure account.
- Navigate to the storage account that contain the file share you want to scan.
- Under Data storage, click File shares.
- Under File share settings, click the file share you want to scan.
- Click Connect.
- Scroll to the code box with the Powershell script.
-
In the Powershell script, take note of the value of /add:, /user:, and /pass:.

These are used as the Target credentials when you scan Azure file shares.
Value of Description /add: This is your Target hostname.
Example: mystorageacct000.file.core.windows.net/user: This is your username.
Syntax: localhost\<Azure-storage-account>
Example: localhost\mystorageacct000/pass: This is your password.
Example: 6CAMRY68DZ8/507kfG7sWDAC63K…uBtw==
Add Azure File Share Target
After getting your credentials, you can now add and scan Azure file shares as a Windows share Target.
- From the New Scan page, add Targets. Refer to the Add Targets section.
- On the Select Target Type window, in the Enter New Target Hostname field, enter the hostname for Azure Files. Your hostname is the name of the Azure storage account with the Azure Files subdomain (the value of /add: e.g., mystorageacct000.file.core.windows.net).
- Click Test. If ER Cloud can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, click on Network Storage.
- Under Network Storage Location Type, select Windows Share.
-
Fill in the following fields:
Field Description Path Enter the path to scan. The path is the name of the file share you want to scan
For example: myfileshareCredential Label Enter a descriptive label for the credential set. Username Enter your username. The username is the value of /user:.
For the guidance instructions, see Get Azure File Share Credentials.Password Enter your password. The password is the value of /pass:.
For the guidance instructions, see Get Azure File Share Credentials.(Optional) Private Key Upload the file containing the private key.
Only required for Target hosts that use a public key-based authentication method. See Set Up SSH Public Key Authentication for more information.Agent to act as proxy host Select a Windows Proxy Agent that matches the Target operating system (32-bit or 64-bit). - Click Test, and then + Add Customized to finish adding the Target location.
If the same location is recognized and scanned by ER Cloud separately as a different location and/or as a different protocol, ER Cloud will count the licensed data usage separately for each individual location.
To prevent redundant scanning and increased counting of licensed data usage, ensure that:
- the same location is not selected for scanning using both Local Storage and Network Storage protocols,
- both the shared folder and its subfolder are not selected for scanning if the subfolder is also shared separately,
- multiple shared folders (all pointing to the same physical location) are not included in the scan, and
- administrative shares are accounted for during location selection for the scan.
For more information and detailed scenarios, see Mitigate Increased Counting of Licensed Data Usage in ER2.
Remediate Azure File Shares
When remediating match locations on Azure file shares using the "Quarantine" option, you can specify a secure location on the Azure Files account storage or in the Windows Proxy Agent host.

Use the following syntax in the "Enter a secure location to quarantine the selected items" field to specify the absolute path to a secure quarantine location on the:
-
Azure Storage account
# Syntax: \\<azure-storage-account>\<name-of-azure-file-share>\<quarantine-folder> \\mystorageacct000\myfileshare\Quarantine-Folder -
Windows Proxy Agent host
# Syntax: <quarantine-folder-on-proxy-agent-host> C:\Quarantine-Folder
Refer to the Perform Remedial Actions section.
Scan Unix File Share (NFS)
Requirements
Select the Unix File Share Target type when scanning a Network File System (NFS) share.
To scan a Unix file share Target:
- Use a Unix or Unix-like Proxy Agent.
- The Target credential set must have the minimum required permissions to access the Target locations to be scanned.
- The Target must be mounted on the Proxy Agent host.
-
The Path field must be set to the mount path on the Proxy host when adding a Unix file share Target.
Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
To mount an NFS share server, on the Proxy host, run as root:
# Requires nfs-common. Install with `apt-get install nfs-common`
mount <nfs-server-hostname|nfs-server-ipaddress>:</target/directory/share-name>
Add Unix File Share Target
- From the New Scan page, add Targets. Refer to the Add Targets section.
- In the Select Target Type window, enter the host name of the Unix file
share server in the Enter New Target Hostname field. This is usually an NFS
file server.
For example, if your Unix file share path is //remote-share-server-name/remote-share-name, enter the Target Hostname as remote-share-server-name:

- Click Test. If ER Cloud can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, click on Network Storage.
- Under Network Storage Location Type, select UNIX File Share.
-
Fill in the following fields:
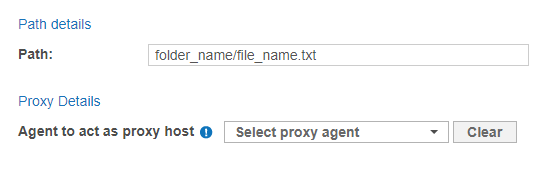
Field Description Path Enter the file path to scan. This is the mount path on the Proxy host for the Unix file share Target.
For example: <folder_name/file_name.txt>.
Agent to act as proxy host Select a Linux Proxy Agent. File share must be mounted on the selected Linux Proxy Agent host. Use the pre-configured Linux cloud Agents to scan cloud Targets only. For the list of Targets according to the type, refer to Target Types in the Add Targets section. For more information about Agents in ER Cloud, refer to the About Enterprise Recon Cloud 2.13.0 section. - Click + Add Customised to finish adding the Target location.
Scan Using Remote Access via SSH
Requirements
To scan a Target using remote access via SSH:
- The Target host must have an SSH server running on TCP port 22.
- The Proxy Agent host must have an SSH client installed.
Supported Operating Systems
ER Cloud supports the following operating systems as remote access via SSH Targets:
| Environment (Target Category) | Operating System |
|---|---|
| Microsoft Windows Desktop (Desktop / Workstation) |
|
| Microsoft Windows Server (Server) |
|
| Linux (Server) |
|
| UNIX (Server) |
|
| macOS (Desktop / Workstation) |
Configure your macOS scans
|
Microsoft Windows Operating Systems
Ground Labs supports and tests ER Cloud for all Windows versions supported by Microsoft.
Prior versions of Windows may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
Linux Operating Systems
Ground Labs supports and tests ER Cloud for all Linux distributions currently supported by the respective providers.
Prior versions of Linux distributions may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
macOS Operating Systems
Ground Labs supports and tests ER Cloud for all macOS versions supported by Apple Inc.
Prior versions of macOS may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
Add Remote Share Target
- From the New Scan page, add Targets. Refer to the Add Targets section.
- In the Select Target Type window, enter the host name of the remote
share server in the Enter New Target Hostname field. The remote share
server must have an SSH server running.

- Click Test. If ER Cloud can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, click on Network Storage.
- Under Network Storage Location Type, select Remote access via SSH.
-
Fill in the following fields:
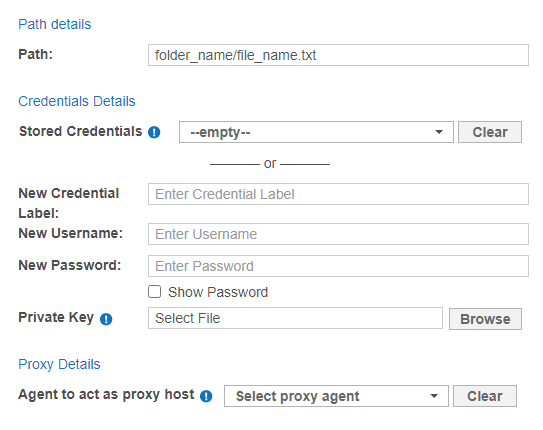
Field Description Path Enter the file path to scan.
For example, <folder_name/file_name.txt>.
Credential Label Enter a descriptive label for the credential set. Username Enter your remote host user name.
Password - SSH password authentication:
Enter your remote host user password. - SSH key pair authentication using private key (password-protected):
Enter the passphrase for the private key. - SSH key pair authentication using private key (non password-protected):
Leave the field blank.
Private Key Upload the file containing the private key compatible with SSH format. For example, userA_ssh_key.pem.
See Set up SSH Public Key Authentication for more information.
The user account on the remote host must be configured to enable SSH key-pair authentication.Proxy Agent Select a Proxy Agent host with direct Internet access. Use the pre-configured Linux cloud Agents to scan cloud Targets only. For the list of Targets according to the type, refer to Target Types in the Add Targets section. For more information about Agents in ER Cloud, refer to the About Enterprise Recon Cloud 2.13.0 section.Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
- SSH password authentication:
- Click Test, and then + Add Customized to finish adding the Target location.
Scan Hadoop Clusters
Requirements
To scan a Hadoop Distributed File System (HDFS) cluster, you must have:
- A Target NameNode running Apache Hadoop 2.7.3 (minimum version), Cloudera Distribution for Hadoop (CDH), or similar.
- A Proxy host running the Linux 3 or 4 Agent with database runtime components for RPM-based Linux systems. Refer to Install Linux 3 or 4 Agent for more information.
- A valid Kerberos ticket if Kerberos authentication is enabled. Refer to Generate Kerberos Authentication Ticket.
Install Linux 3 or 4 Agent
To install the Linux 3 or 4 Agent with database runtime components:
- On the designated Proxy host, go to the Web Console and navigate to Settings > Agents > Node Agent Downloads.
-
In the list of Node Agents available for download, select the Linux 3 64bit (Red Hat) (RPM) * or Linux 4 64bit (Red Hat) (RPM) * Agent.
Make sure that the Agent installation package has "database-runtime" in its Filename. -
To install the Linux 3 64bit (Red Hat) (RPM) * or Linux 4 64bit (Red Hat) (RPM) * database runtime Agent, run the following commands in a terminal on the designated Proxy Agent host:
# Remove existing ER2 packages rpm -e er2
# Install the epel-release package yum install epel-release
# Install the required packages yum install libxml2 libgsasl openssl libcurl libuuid protobuf krb5-libs libaio
# Install the Linux 3 or 4 Agent, where 'er2-2.x.x-linuxx-rh-x64_database-runtime.rpm' is the location of the rpm package on your computer. rpm -ivh er2-2.x.x-linuxx-rh-x64_database-runtime.rpm - (Optional) Generate Kerberos Authentication Ticket.
Generate Kerberos Authentication Ticket
If Kerberos authentication is enabled for your HDFS cluster, run the following commands in a terminal on the designated Proxy Agent host.
To generate a Kerberos ticket:
-
(Optional) Check if a valid Kerberos ticket has been issued for the principal user:
klist -
Generate a Kerberos ticket as a principal user:
# kinit <username>@<domain> kinit userA@example.com
To renew an expired Kerberos ticket:
-
If the ticket has expired within its renewable lifetime:
# kinit -kt '<path to keytab file>' <username>@<domain> kinit -kt '/home/hadoop/userA.keytab' userA@example.com -
If the ticket has expired beyond its renewable lifetime:
kdestroy
# kinit <username>@<domain> kinit userA@example.comRunning the kdestroy command destroys all of the user's active Kerberos authorization tickets.
- Generate a New Kerberos Authentication Ticket if the ticket validity expires while the scan is still in progress, or
- Generate a Kerberos authentication ticket with a ticket lifetime that is valid for the duration of the scan.
Add Hadoop Target
- From the New Scan page, add Targets. Refer to the Add Targets section.
- In the Select Target Type window, enter the host name of the NameNode
of the HDFS cluster in the Enter New Target Hostname field.
For example, if your HDFS share path is hdfs://remote-share-server-name/remote-share-name, the host name of the NameNode is remote-share-server-name. Enter the Target Hostname as remote-share-server-name:

- Click Test. If ER Cloud can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, click on Network Storage.
- Under Network Storage Location Type, select HDFS.
- Fill in the following fields:
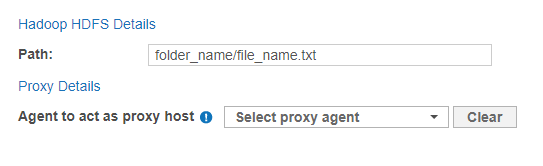
Field Description Path Enter the file path to scan. For example, <folder_name>/<file_name>.
If the NameNode is accessed on a custom port (default: 8020), enter the port before the HDFS file path: (port=<port>)<folder_name>/<file_name>.
For example, to scan a Hadoop cluster with NameNode accessed on port 58020, enter (port=58020)folder-A/file-A.txt.Proxy Agent Linux 3 or 4 Agent with database runtime components. Use the pre-configured Linux cloud Agents to scan cloud Targets only. For the list of Targets according to the type, refer to Target Types in the Add Targets section. For more information about Agents in ER Cloud, refer to the About Enterprise Recon Cloud 2.13.0 section. -
Click + Add Customised to finish adding the Target location.
Recommended Least Privilege User ApproachTo reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.