Enterprise Recon 2.11.0
Agentless Scan
This section covers the following topics:
- Overview
- How an Agentless Scan Works
- Agentless Scan Requirements
- Supported Operating Systems
- Start an Agentless Scan
Overview
You can use ER2 to perform an agentless scan on network Targets via a Proxy Agent. Agentless scans allow you to perform a scan on a target system without having to:
- Install a Node Agent on the Target host, and
- Transmit sensitive information over the network to scan it.
Use agentless scans when:
- The Node Agent is installed on a host other than the Target host.
- Data transmitted over the network must be kept to a minimum.
- The Target credential set has the required permissions to read, write and execute on the Target host.
- The Target host security policy has been configured to allow the scanning engine to be executed locally.
For more information, see Agentless Scan Requirements below.
How an Agentless Scan Works
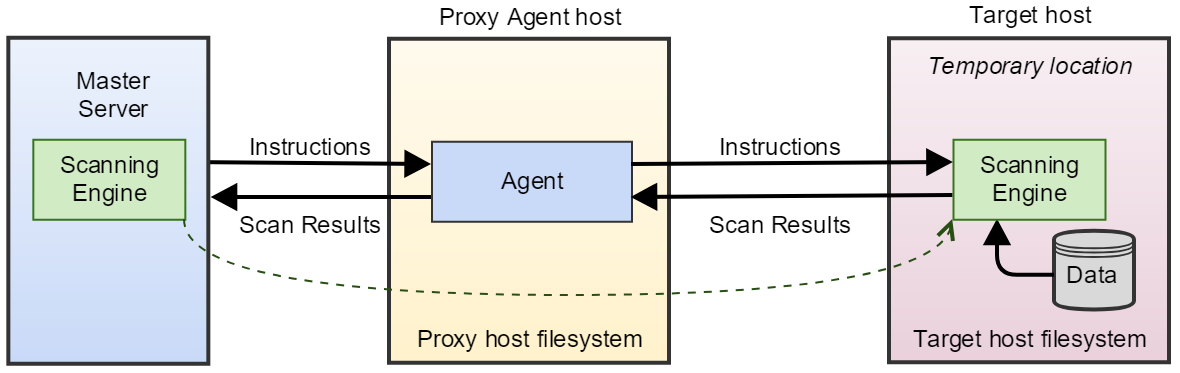
When an agentless scan starts, the Proxy Agent receives instructions from the Master Server to perform a scan on a Target host. Once a secure connection to the Target host has been established, the Proxy Agent copies the latest version of the scanning engine to a temporary location on the Target host.
The scanning engine is then run on the Target host. It scans the local system and sends aggregated results to the Proxy Agent, which in turn sends the results to the Master Server. Data scanned by ER2 is kept within the Target host. Only a summary of found matches is sent back to the Master Server.
Once the scan completes, the Proxy Agent cleans up temporary files created on the Target host during the scan and closes the connection.
Agentless Scan Requirements
Make sure that the Target and Proxy Agent host fulfill the following requirements:
| Target Host | Proxy Agent | TCP Port 1 | Requirements |
|---|---|---|---|
| Windows host | Windows Proxy Agent |
For Targets running Windows Server 2008 and newer:
For Targets running Windows Server 2003 R2 and older:
WMI can be configured to use static ports instead of dynamic ports.
|
|
| Linux or UNIX host | Windows, Linux or UNIX Proxy Agent |
|
|
| macOS host | macOS Proxy Agent |
|
|
1 TCP Port allowed connections.
Before embarking on this approach, Ground Labs recommends consideration of the Agent-based scanning approach which can achieve data discovery with a reduced level of user permission whilst offering other performance benefits.
Supported Operating Systems
ER2 supports the following operating systems as agentless scan Targets:
| Environment (Target Category) | Operating System |
|---|---|
| Microsoft Windows Desktop (Desktop / Workstation) |
|
| Microsoft Windows Server (Server) |
|
| Linux (Server) |
|
| UNIX (Server) |
|
| macOS (Desktop / Workstation) |
Scans for macOS Monterey 12.0 and above
Agentless scans for macOS Ventura 13 and above
Performing agentless scans requires the "Full Disk Access" feature to be enabled for sshd-keygen-wrapper in the Proxy Agent host. See Enable Full Disk Access for more information. |
Microsoft Windows Operating Systems
Ground Labs supports and tests ER2 for all Windows versions supported by Microsoft.
Prior versions of Windows may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
Linux Operating Systems
Ground Labs supports and tests ER2 for all Linux distributions currently supported by the respective providers.
Prior versions of Linux distributions may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
macOS Operating Systems
Ground Labs supports and tests ER2 for all macOS versions supported by Apple Inc.
Prior versions of macOS may continue to work as expected. However, Ground Labs cannot guarantee support for these versions indefinitely.
Start an Agentless Scan
To perform an agentless scan on a Target:
- Log in to the ER2 Web Console.
- Navigate to the Select Locations page by clicking on:
- Scans > New Scan, or
- the New Scan button in the Dashboard, Targets, or Scans > Schedule Manager page.
- On the Select Locations page, click + Add Unlisted Target.
- In the Select Target Type window, choose Server and enter the host name of the Target in the Enter New Target Hostname field.
- Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- In the Select Types dialog box, select Target locations from Local Storage or Local Process Memory, select the Target type, and click Done.
- In the New Target page:
- Assign Target Group - Assign the Target to the Target Group selected from the dropdown box.
-
Specify the Operating System of the Target - Select the operating system for the Target host from the dropdown box.
Ensure that you select the correct operating system for the Target host. Certain features in ER2 (e.g. PRO Data Classification with MIP, PRO Data Access Management) may not work as expected if the selected operating system is incorrect or is set to "Remote Access Only".
- Click Next.
- The UI prompts you if there is no usable Agent detected on the Target host. Select Would you like to search this target without installing an agent on it? to continue.
-
Fill in the following fields and click Next:
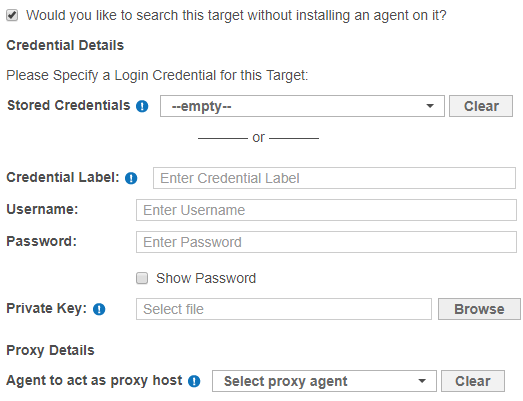
Field Description Credential Label Enter a descriptive label for the credential set. Username Enter your Target host user name. Password Enter your Target host user password, or passphrase for the private key. (Optional) Private Key Upload the file containing the private key.
Only required for Target hosts that use a public key-based authentication method. See Set Up SSH Public Key Authentication for more information.Agent to act as proxy host Select a suitable Proxy Agent. - On the Select Data Types page, select the Data Type Profiles to be included in your scan and click Next. See Data Type Profiles.
- Set a scan schedule in the Set Schedule section. Click Next.
- Review your scan configuration. Once done, click Start Scan.