
Begin your data journey
Discover how Ground Labs uncovers hidden sensitive data, simplifies compliance, and gives you full visibility—anywhere your data lives.
Ground Labs empowers organizations to uncover hidden sensitive and personal data wherever it lives – in the cloud or on-premises, across structured or unstructured data. Gain complete visibility, simplify compliance and proactively reduce risk, all with one powerful solution.
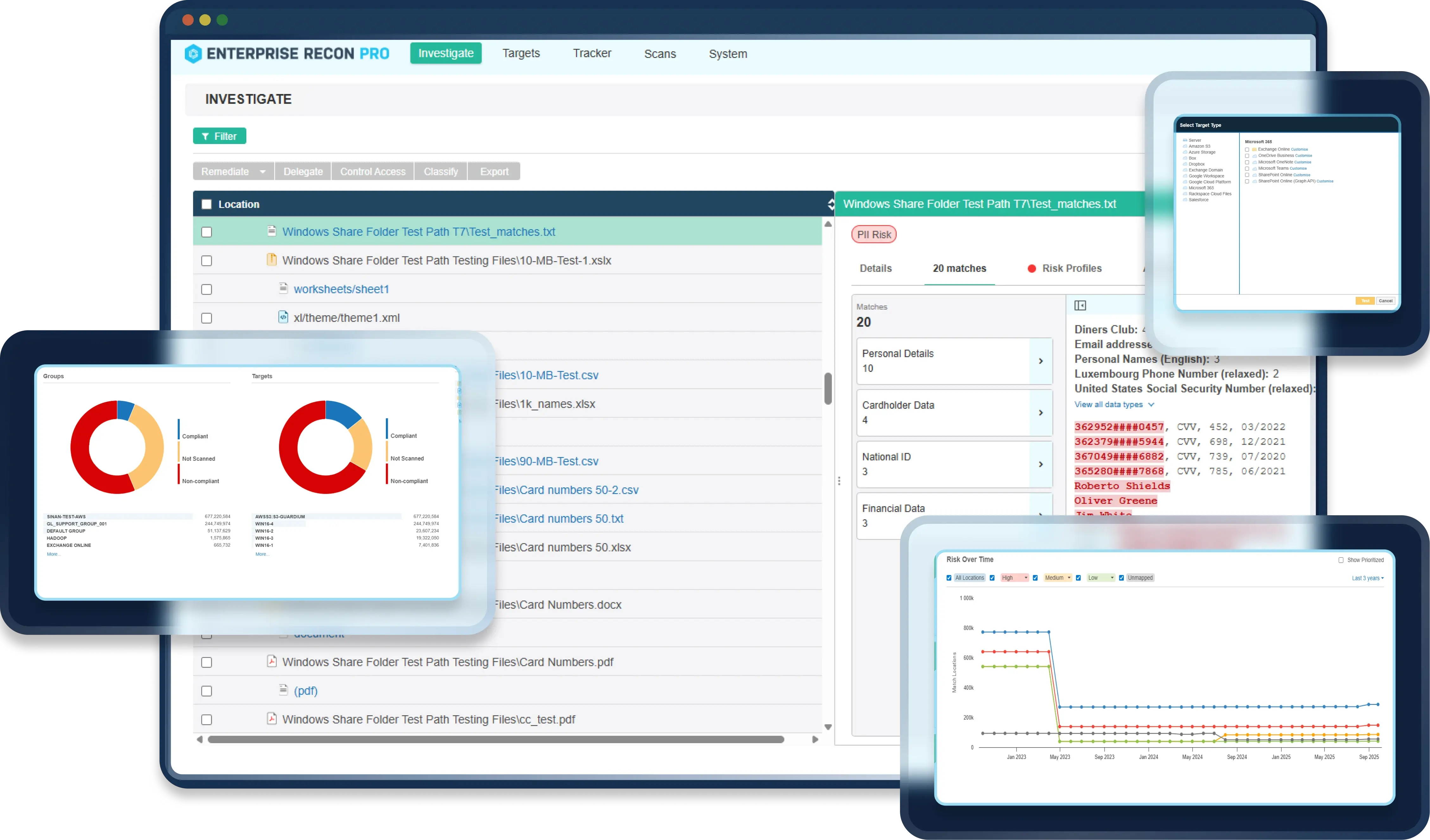







Providing visibility of all sensitive data wherever it is stored, Ground Labs’ award-winning
data discovery solutions deliver streamlined data management capabilities for security,
privacy and compliance.
Up to 90% of business data is unstructured, and nearly half lives in the cloud. With breaches now a matter of “when” not “if” and regulatory obligations growing ever more complex, keeping your data safe has never been harder.
Watch the video to learn how Ground Labs can help >

Whether you need enterprise-wide visibility, PCI compliance, or developer-ready tools,
Ground Labs provides solutions built to uncover and protect sensitive and personal data everywhere it lives.
We enable customers to tackle the growing complexity of unstructured data, cloud risk, and regulatory obligations with practical, innovative solutions.
Aswini R.
PCI AdminBest thing about ER is the comprehensive data discovery capabilities, which allow for accurate identification of sensitive information across diverse environments. The interface is user friendly, and the platform is intuitive, making it accessible even to non-technical users.
Gaurav D.
Security AssuranceOur primary use case was identifying and managing personally identifiable information across a diverse set of structured and unstructured data sources. Enterprise Recon consistently delivered high accuracy with notably low false positive rates
Kelvin H.
Consulting Practice DirectorEnterprise Recon is the go-to solution for discovery of sensitive data at rest. It is very effective at detecting stored cardholder data, PII data or other sensitive data.
James J.
CTOEnterprise Recon was a cornerstone of our PCI compliance toolkit. Deployed across desktops, servers, and cloud storage, its SaaS platform and lightweight agents gave us full visibility into unstructured data with minimal overhead. Truly “fire-and-forget,” it ran reliably in the background until action was needed.
Bruce T.
PCI Technical AdvisorWe’ve used Enterprise Recon for over 7 years across our entire PCI environment. It works on any device or OS, makes suspect data easy to remediate, and lets you set filters to reduce false positives. You can also schedule recurring scans and receive notifications of the results.
Shannon M.
Support Desk AnalystEasy to use, simple to maintain. Support is fantastic, the team greatly assisted me in picking up the software for a refreshed integration and implementation for our environment. Overall solid PCI scanning product that is unmatched in the field









Add to this the fact that compliance regulations continue to emerge as cybercriminals increase their
sophistication, and organizations have a massive problem on their hands.

Discover how Ground Labs uncovers hidden sensitive data, simplifies compliance, and gives you full visibility—anywhere your data lives.